Qantas Data Breach: Latest Update, Class Action Details & Compensation
Qantas is under pressure after hackers stole data from 5.7 million customers. The airline now faces a class action over the breach.
Qantas has confirmed that the personal data of 5.7 million customers has been compromised as part of a cyberattack against the airline. The attack occurred on 30 June 2025, and was revealed by Qantas two days later, blamed on a third-party platform used by Qantas’ call centre in Manila.
Adding further pressure, leading law firm Maurice Blackburn has launched a class action against Qantas, alleging the airline failed to adequately protect customer data.
Qantas has call centres in multiple worldwide locations including Australia, New Zealand, South Africa, Fiji and the Philippines. If you have ever interacted with the Manila contact centre, it’s likely your data will have been stored in that system, and is now compromised.
In a recent statement, Qantas has provided a clearer picture of the incident and how it responded, as well as what compensation its Frequent Flyers can expect. Qantas also confirmed it has been contacted by a "potential cybercriminal" and is working with the Australian Federal Police to verify the legitimacy of that contact.

Qantas CEO Vanessa Hudson would not confirm or deny if the airline has been asked to pay a ransom, or what the company's policy was regarding ransom demands.
“Our absolute focus since the incident has been to understand what data has been compromised for each of the 5.7 million impacted customers and to share this with them as soon as possible....we have put in place a number of additional cyber security measures to further protect our customers data, and are continuing to review what happened."
Class Action Launched Over Qantas Hack
In the wake of Qantas’ cyber hack, law firm Maurice Blackburn has launched a Class Action against the airline. Maurice Blackburn is widely referred to as Australia's leading class actions law firm, having won more than $5 billion in class actions recoveries since 1998.
“We’ve filed an official complaint with the Office of the Information Commissioner, which is the authority charged with taking action over breaches of the Privacy Act,” says principal lawyer Elizabeth O’Shea.
“It is early days in what we are learning about the mass data breach, but if you’re one of the millions of people that have had your personal information compromised, you’re eligible to register with us.”
The claim, filed on 17 July 2025, argues that Qantas failed to adequately protect the personal information of its customers.
You can register for the Qantas Data Breach Class Action on Maurice Blackburn’s website. Registering will not expose you to any cost unless and until there is a successful outcome. Legal costs are the responsibility of Maurice Blackburn.

What Data Was Stolen In The Qantas Hack?
Following forensic analysis, Qantas has now outlined the types of data exposed in the breach. This will vary by customer, and the Flying Kangaroo reinforced that there is currently no evidence that any stolen personal data has been released.
The Qantas investigation found that 5.7 million unique customers' data has been compromised. Specific data fields vary from customer to customer.
- 4 million customers had tier names, email addresses and Frequent Flyer details exposed.
- Of these, 1.2 million records included only a name and email address.
- The remaining 2.8 million also included Frequent Flyer numbers, with some listing membership tier, points balance or Status Credits.
- A further 1.7 million customers have had a combination of the above and one or more of the following leaked
- residential or business address (1.3 million)
- date of birth (1.1 million)
- phone number (900,000)
- gender (400,000)
- meal preference (10,000)
While Qantas insists that the stolen data is “not enough to gain access” to any Frequent Flyer account, the exposed information is still highly valuable to scammers. No passwords, login details or PINs were compromised, and Qantas systems themselves remain unaffected.
Will Qantas Compensate Customers?
When approached by Flight Hacks, a spokesperson for Qantas was unable to confirm whether the airline has plans to issue Qantas Points, flight credits or other forms of apology to affected customers. But Qantas is offering assistance via a dedicated 24/7 cyber support hotline, which can provide specialist identity protection advice and resources. Customers can access the hotline on 1800 971 541 or +61 2 8028 0534.
Flight Hacks called the support centre earlier today and was told by the agent that most Qantas cyber hotline calls are being sent to an overseas call centre in the United Kingdom. On the topic of compensation, we were told to keep an eye out, as it was a possibility but not yet official.
Qantas Is Contacting Customers Whose Data Was Stolen
From 9 July, Qantas started directly contacting affected customers via email to advise which specific data fields were included in their compromised records. These emails are being sent progressively, with the process expected to be completed within 24 to 48 hours.
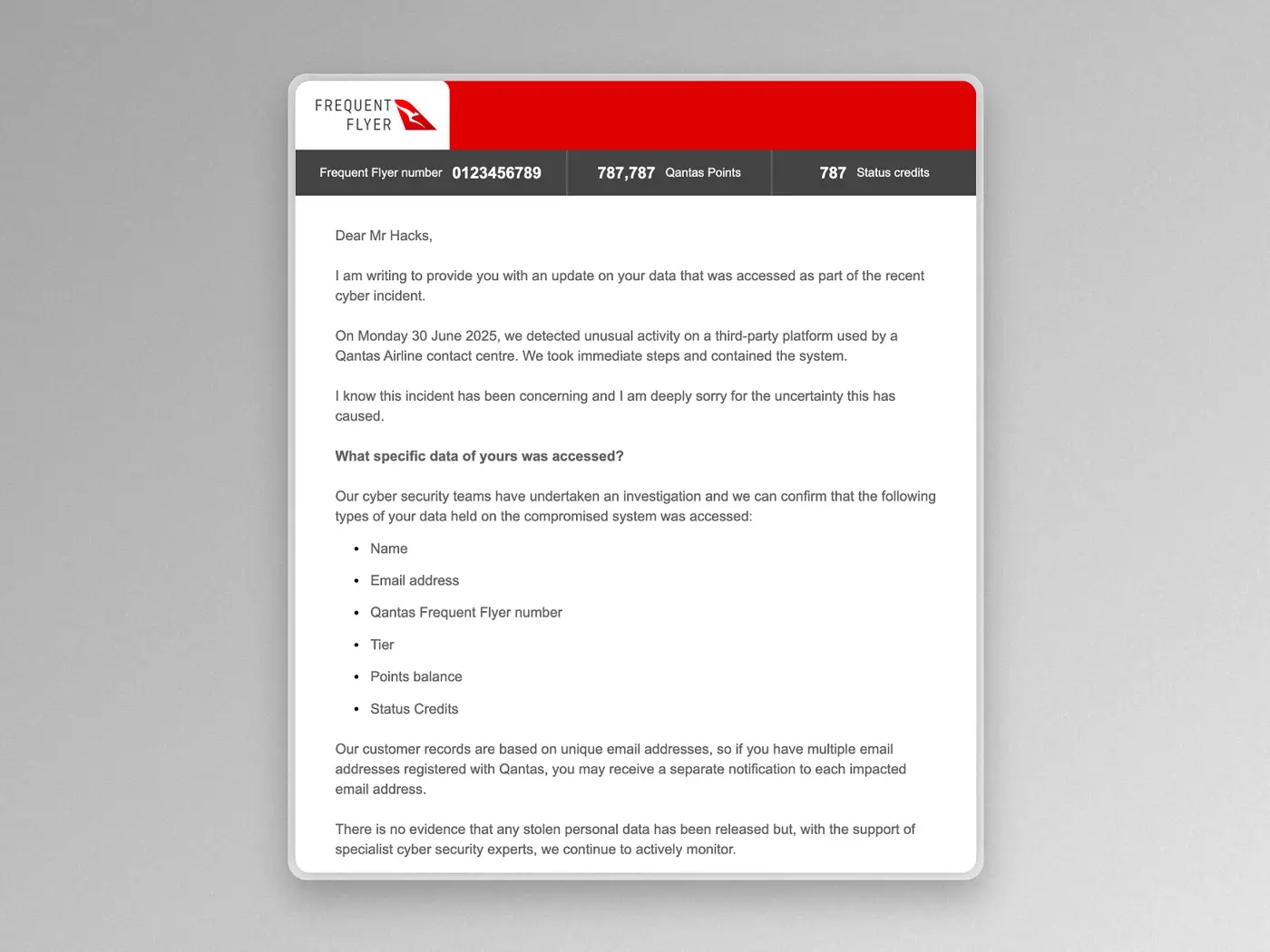
With that in mind, it is important to protect yourself, as scammers will most likely use the leaked information to pose as Qantas employees. With so much detail already in hand, they may convince some people to transfer money or hand over credit-card details.
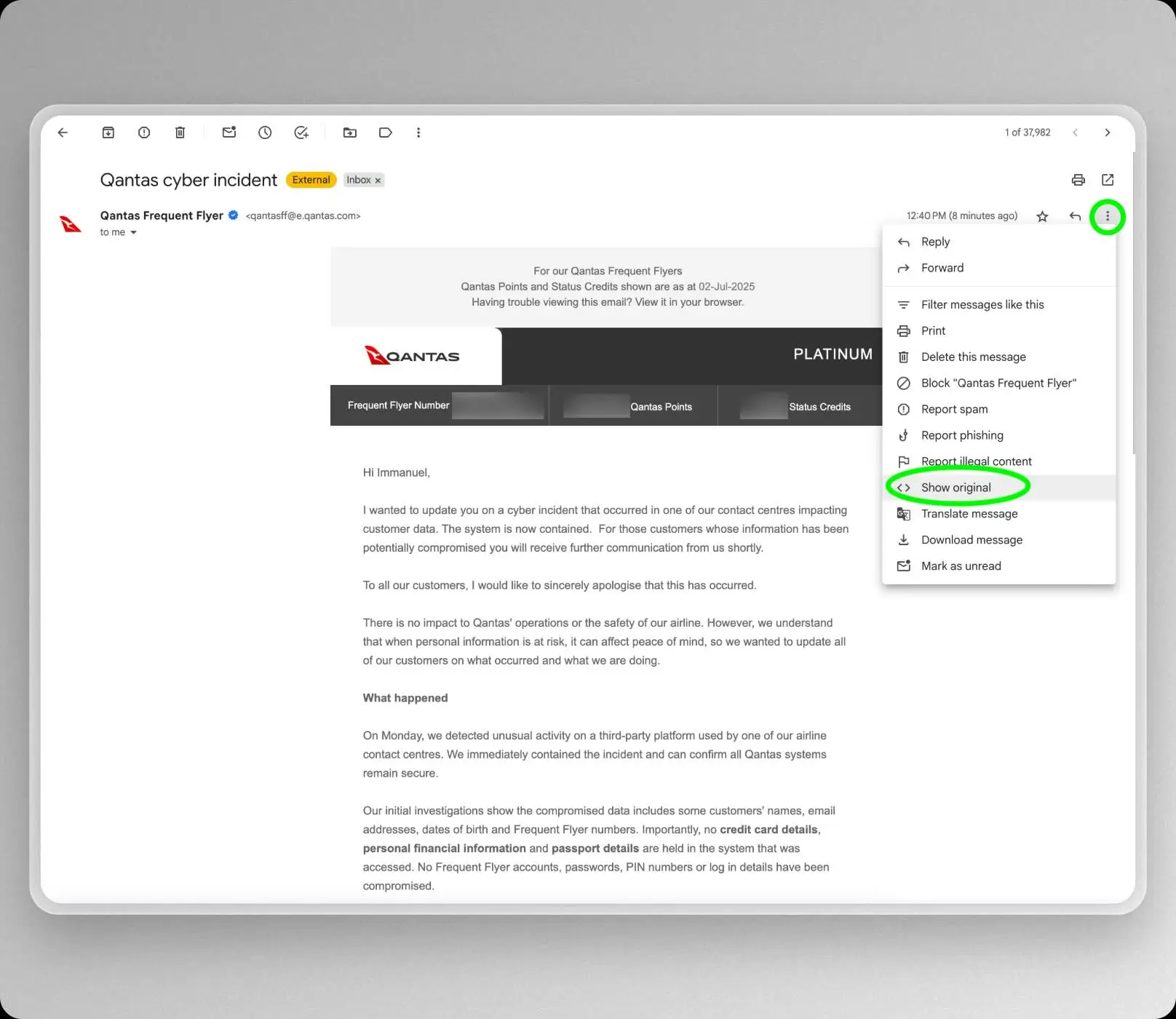
If you use Gmail, verifying the sender of an email is simple:
- Click the three dots beside the message.
- Select Show original.
- Look for DKIM and DMARC results. If you see dkim=pass and a matching DMARC pass for qantas.com, the message originated from Qantas’ authorised platform.
Even when those signatures pass, always keep common sense in mind. For payments, password resets or personal-data requests, leave the email and log in directly through the Qantas app or website, or call the airline. The number-one rule is never to give personal or payment details to anyone who contacts you first, no matter how urgent they make it sound.
What Is Qantas Doing To Prevent Further Attacks?
Qantas is working to understand which data was accessed and to communicate transparently with affected customers. Since the incident, Qantas has put in place a number of additional security measures, including;
- Additional security controls on frequent flyer accounts, including requiring additional identification for account changes..
- Further restricted access to the third-party platform in the Manila contact centre.
- Increased system monitoring and detection for unusual activity.
Related posts








